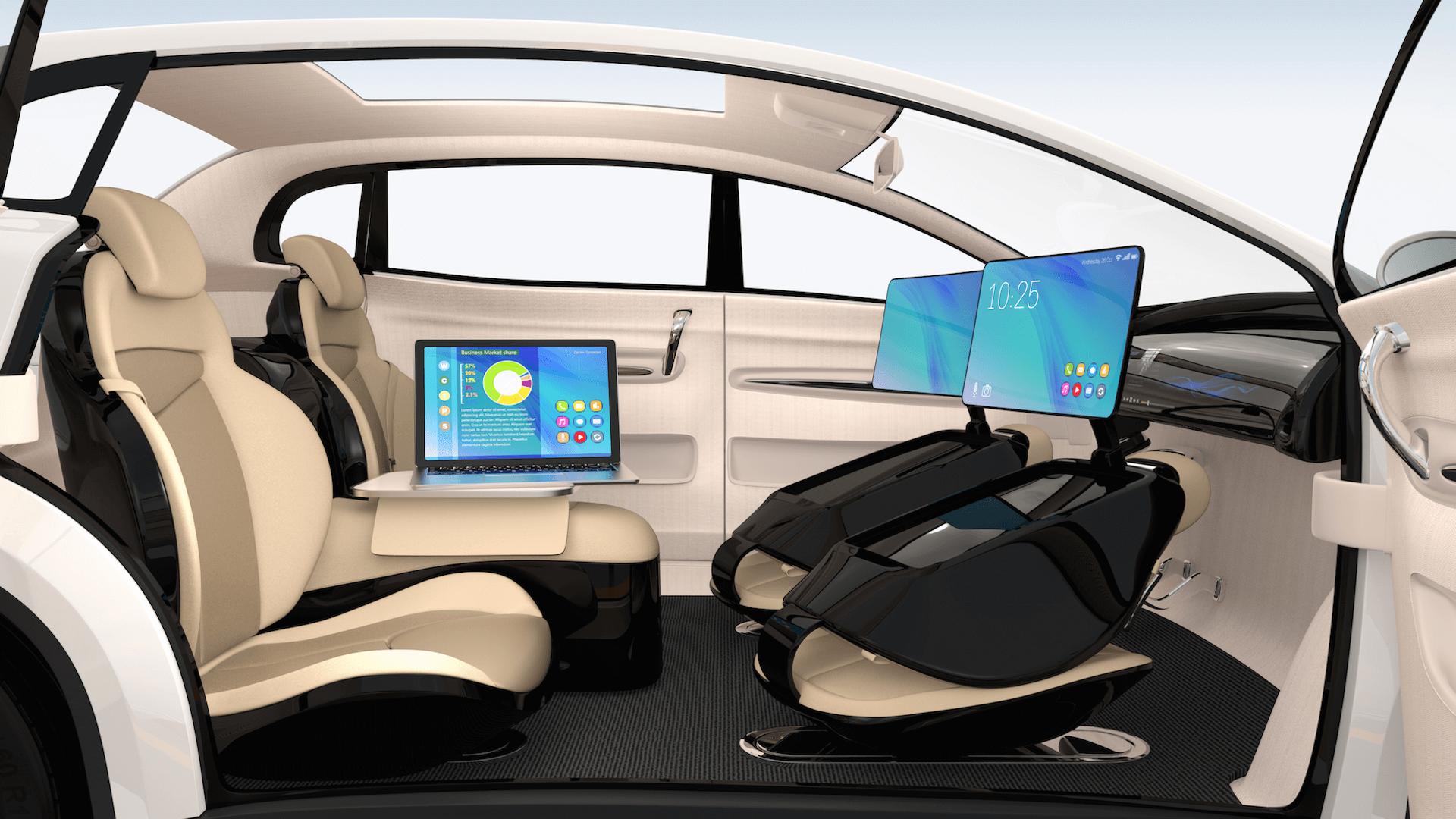
FCEVs, Ideal for Autonomous Driving?
Hydrogen Fuel Cell Electric Vehicles (FCEVs) might help Autonomous vehicles go mainstream. Autonomous vehicles are generally defined as vehicles capable

Hydrogen Fuel Cell Electric Vehicles (FCEVs) might help Autonomous vehicles go mainstream. Autonomous vehicles are generally defined as vehicles capable
Power Electronics Engineers according to Schweitzer Engineering Laboratories, Inc., is “one of the oldest branches in engineering.” As new branches

Use of Drones in Different Industries In terms of the technological advancement that the aviation industry has seen in the
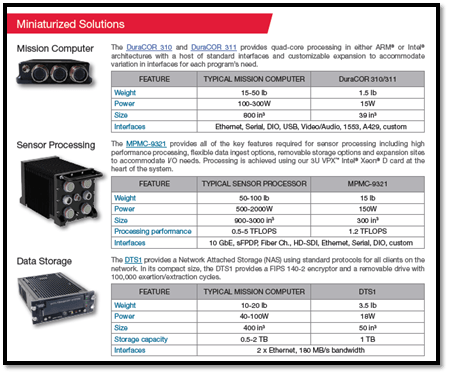
SWaP-C what it is, what it means to the Aircraft industry. When it comes to the design and operation of
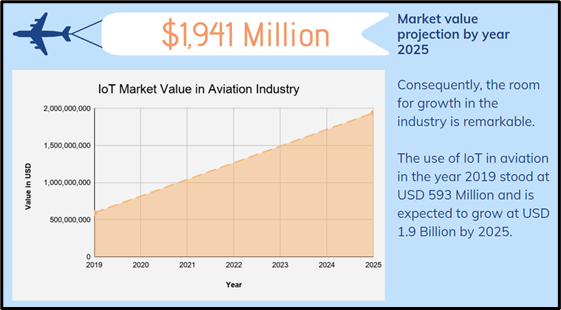
The use of IoT technology allows different types of sensor to monitor, locate, and report specific data to centralized servers

Embracing next technology healthcare without adequate preparation will only open new risk avenues and threat vectors for healthcare cyber attacks.

Ransomware is distributed as a social engineering ploy via email, malicious links and malvertizing, among other techniques. A proactive ransomware

Healthcare is unprepared for cyber attacks and as the cybercrime threat landscape for medical devices and electronic health records is

When the United States’ military stealth tech bomber was rumored and then when it made a public debut, it was

Comprehensive pre-employment background checks are an absolute necessity. Your time is a valuable commodity. When you consider taking on a
We are known for finding the “needle in the haystack” and discovering “diamonds in the rough”. With our award-winning Leadership Vault search process, we identify & recruit top producers in senior management, functional leadership, & key senior roles.
Aerospace / AVT – Chicago (630) 378-0005
AI / IoT | Wireless – Orlando (386) 693-1940
Industry 4.0 / Power Electronics – St. Louis (636) 489-3888
NextGen Global Executive Search LLP

Orlando, FL
Discuss your C-level, functional leadership, or key staffing needs for strategy, sales, and business development roles in the wireless ecosystem including 5G MNOs, ORAN infrastructure systems, LBS services; and all roles within Digital Transformation (CX, CDP, DMP) and IoT (data, devices, networks).

Chicago, IL
Discuss your C-level, functional leadership, or key staffing needs for aircraft electrical power generation systems, aviation cabin and in-seat power supplies and converters, MEA, aerospace precision parts manufacturing, military aircraft, drones, hydrogen fuel cells, and industrial power electronics.

St. Louis, MO
Kelley focuses on providing FIRST CLASS level service to her clients and candidates under all circumstances without any expectations in return. This level of service has afforded her a network of relationships with superstar individuals who are all “A” Players.

Get notified about new articles, videos, seminars and all the breaking industry news as it happens