The truth of the matter when engaging a retained search firm for multiple key staffing needs is they produce far better candidates, have much deeper relationships in the industry they are working in and have a search process that in the end delivers candidates who can meet or exceed the objectives of the role in which they are hired into.
Many company’s HR and Talent Acquisition groups think more short term than long term when it comes to staffing critical roles. The long term strategy is most often used – a combination of career site branding, job boards and job aggregators, LinkedIn talent solutions, and using multiple contingency search firms to help build a large database of potential candidates.
What is missing is that for critical roles that must be filled with quality new hires, the long-term strategy rarely works. Even though using RPOs and contingency search firms will result in the most resumes, it is pure folly to believe quality is the main driver produced by those outsourced means. Therefore, engaging a retained search firm is the best of all options when outside recruitment help is needed.

Let’s look at the recognized statistics in the global workforce. The majority of all workers – approximately 55%, are “C players”. They are literally just bodies taking up space.
They show up on time, can perform assigned tasks assigned such as software or QA engineer, customer service, inside sales, operations, manufacturing and production roles. But the reality is that they don’t develop intellectual property or design anything new;
They are not problem solvers, entrepreneurial or creative and contribute virtually nothing to increasing market share or improving P&L ratios. In addition, many “C players” are just not good employees. Often a lack of upwardly mobile skills, education, and more equates to lack of motivation outside of a repetitive paycheck.
Next are the “B players” who make up to 35% of the workforce, have real education and skills, contribute to developing IP, producing revenues, or some other vital contribution. However, the cream of the crop is approximately 14% of the workforce known as “A players”. From janitor to CEO every type of role has their “A players”. What is so great about hiring them? Leadership IQ and SHRM have developed studies and surveys that demonstrate that “A” players” produce 8 to 10 TIMES MORE than even “B players”.
Reasons for Engaging a Retained Search Firm
With over 30 years of experience in the executive search business, we have rarely seen contingency search firms or RPOs deliver “A players” and have no consistency in delivering “B players” for clients to consider. How do we know this?
- In a less than a 5% unemployment rate environment, most exceptional professionals are happy where they are now in terms of their role, their employer, and compensation. If they were to become passive candidates and look to make a change due to desiring new challenges or relocation, they would simply network and reach out to hiring managers in their industry directly. They rarely look at job postings and have no need to post their resume to a job board. They will not fill out an online application on any company career web site. They are bombarded with emails, InMail’s, and calls every day from corporate recruiters and contingency search firms who generally speaking fail to understand these professionals will likely only speak or reply to an actual executive hiring manager or a retained executive search consultant with a solid reputation among industry Board of Directors and CXOs.
- Contingency and RPO firms rely heavily on job postings and job aggregators. But many of those applicants are the unemployable, unemployed, or “C players”.
- In large contingency search firms the recruiters are graded on the number of send outs (resumes that need to be sent daily to meet a quota). And RPOs have a LOT of clients. Ask yourself, as a client, how much of a priority are you to a recruiter working on 12 to 25 searches at a time? What type of quality and search process would you expect?
I’m not knocking contingency recruiters. I used to be one before I changed to retained almost 20 years ago. Why did I make that move? One, I realized to really have clients as a priority and deliver a superior service, I personally could only work on 3 to 4 searches at a time. To do more than that means both the client and my reputation suffer. Two, with using a search process that was very sound I knew the methodology would unearth those “A players” so I could assess and deliver proof that the shortlisted candidates I presented could meet or exceed the expectations and objectives of the role and client required of the new hire.
As for cost and benefit analysis, the benefits of using retained search is overwhelming while the costs are not much different than contingency search fees.
- When looking to engaging a retained search firm, you are assured that the vetting and development process are superior as you usually receive only 3-4 shortlisted candidates for each role.
- Retained Search provides detailed interview and assessments including current / prior KPIs, depth of industry relationships, and similar accomplishments relevant to the new role.
- Team fit analysis and Target Candidate Profile – by conducting brief online surveys of the stakeholders for each role (team the role will work within and key internal customers), a team profile allows the recruiter to use behavioral analysis and assessment to determine how the potential candidate will fit in and affect team dynamics. One-way behavioral testing of candidates never works as it fails to have anything to measure against.
- Much longer retention of new hires from retained search firms. For instance, 94% of our placements are still working for that client after 4.5 years.
- Superior Replacement guarantee – most contingency firms incorporate a 30 to 90 days refund or replacement. Retained search firms are often 6 to 12 months. We believe in our process so much that we offer 24 to 36 months replacement guarantee depending on the assignment.
- Success based search fees – this is relatively new for retained search firms but a practice we have used for the last 5 years. With most large retained search firms, you pay 100% of the fee regardless if the outcome was successful. Other search firms like NextGen Global Executive Search are performance based. After the initial deposit, the remainder of the fees are paid based on deliverables, including the hire.
- Flat based fees – this is also a relatively new concept. This arose out of the obvious conflict of interest associated with compensation-based search fees. If the recruiter negotiated a higher compensation that was agreed to by both client and candidate, the search fee increased. While some retained search firms use the same fee for every search on a flat fee basis, at NextGen we realized we are being paid for our work. Therefore the basis of the flat fee is appropriate to each role depending on factors such as limitations on relocation, the actual candidate pool size, the number of hours expected in research, search strategy, recruiting, and delivery.
For instance we have clients in the Bay area, NYC and Boston who funny as it sounds believe few exist outside their geography that are worthy of consideration as they often think of themselves as the center of the technology universe. Additionally, for some roles the candidate pool overall is small such as AI architects and power electronics design engineers.
Engaging a Retained Search Firm for filling multiple roles
As retained search firms are like good lawyers and executive management consultants, we ask for a deposit,. This means the client is a priority as they have “skin in the game”, knowing the search firm has a track record in longer retention and producing exceptional new hires. So, the overall flat search fees mean that engaging a retained search firm is clearly the best choice.


 Even the traditional retained search model, which does produce much better candidates, is going by the wayside. More and more companies are ditching recruiting firms that are traditional retained search models.
Even the traditional retained search model, which does produce much better candidates, is going by the wayside. More and more companies are ditching recruiting firms that are traditional retained search models.
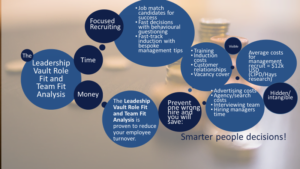 Figuring out exactly the kind of candidate you’re looking for and creating a job description to match can be a time‐consuming headache. But a simple job survey of the direct stakeholders to the role you are recruiting for, lasting around 12-14 minutes, will produce detailed analysis on how those stakeholders view the role and a composite team analysis on these FOUR POINTS:
Figuring out exactly the kind of candidate you’re looking for and creating a job description to match can be a time‐consuming headache. But a simple job survey of the direct stakeholders to the role you are recruiting for, lasting around 12-14 minutes, will produce detailed analysis on how those stakeholders view the role and a composite team analysis on these FOUR POINTS:







 Here are three points why increasing new hire productivity works when behavioral assessments are used properly. What is a general consensus among most companies is this usually involves a questionnaire that asks the candidate about their opinions, preferences and priorities.
Here are three points why increasing new hire productivity works when behavioral assessments are used properly. What is a general consensus among most companies is this usually involves a questionnaire that asks the candidate about their opinions, preferences and priorities.