Customer experience, more precisely online interactions and digital experiences. has been marked by an unprecedented shift due to the recent pandemic.
According to the Adobe Digital Economy Index, U.S. e-commerce spending is expected to total between $850 billion and $930 billion this year, reaching $1 trillion in 2022. Research indicates that 72% of all e-commerce transactions will be attributed to mobile in 2021, which is unsurprising given changing consumer behaviors that drive demand for diverse mobile applications. Between 2021 and 2025, the mobile apps market is positioned to increase by $653.91 billion, advancing at a CAGR of nearly 21% throughout the forecast period.
The proliferation of Internet of Things (IoT)-connectivity is further contributing to market growth of mobile applications because IoT data enables various functionalities that can generate consumer-to-brand touchpoints. Organizations are using IoT data as a critical component in personalization and engagement to improve the CX and deliver category-defining mobile experiences.
Globally, connected IoT devices are on track to grow to 30.9 billion units by 2025, which presents a number of opportunities if organizations have the capabilities to effectively harness IoT data and leverage advanced analytics to significantly improve the CX.
Customer data platforms (CDP) enabled with IoT capabilities play a vital role in helping organizations obtain a greater understanding of customer data and behaviors, and the capabilities to leverage that data for personalized, digital-first experiences.
Capitalizing on the Potential of IoT
As more devices and consumer products become connected to the internet, customer expectations of engagement with a business is fundamentally altering. Salesforce research indicates that for 80% of customers, the experiences that a company delivers are as important to them as products and services.
Consider Starbucks, who uses IoT data to create omnichannel experiences that are widely acknowledged as best-in-class. For example, Starbucks has disrupted the loyalty rewards program model by making it possible to reload cards on any channel, and any modifications to a profile or card is updated in real-time throughout all channels. They use IoT data to better understand customer preferences and trends, reduce potential bottlenecks at drive-thru windows, and allow customers to directly trace their coffee source.
Organizations need to capitalize on the CX potential of IoT data via solutions like IoT-enabled CDP. CDP solutions enable first-party data to be collected and unified, providing a cohesive view of the customer. It also eliminates fragmented data and marketing silos by connecting other systems and marketing tools to create a centralized source of truth for customer data.
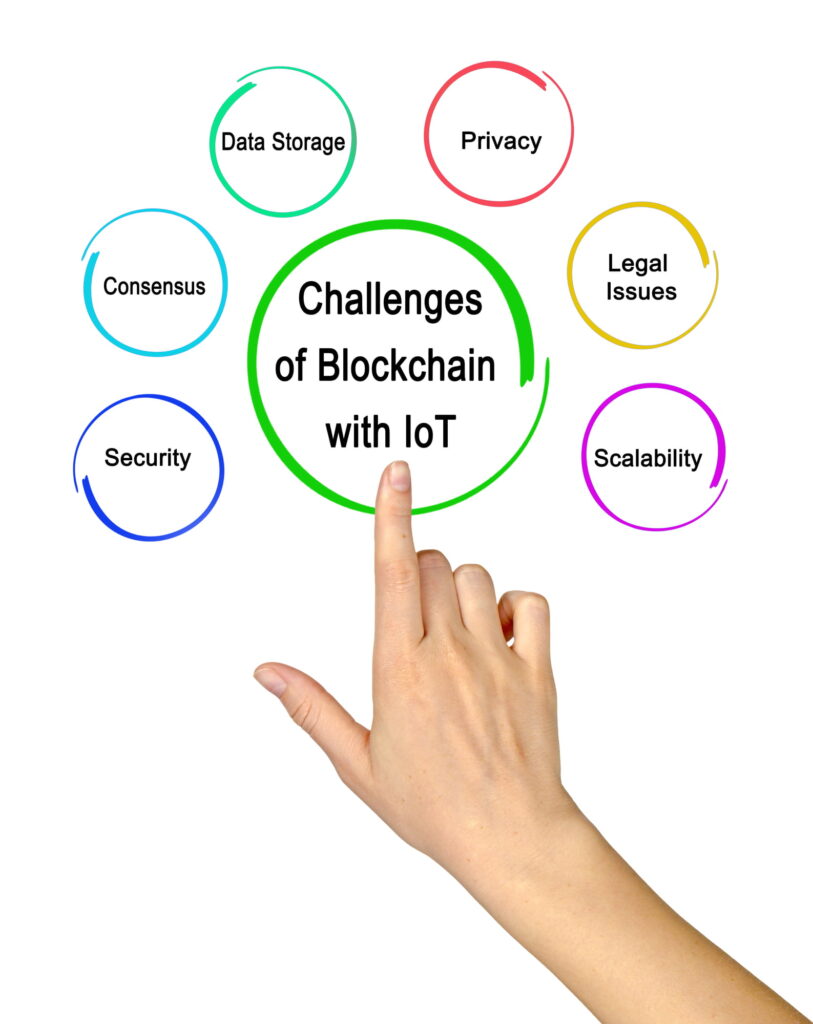
IoT data, however, is simultaneously a challenge and an opportunity.
 On one hand, IoT generated data is sensitive, which impacts regulatory and compliance protocols. Additionally, IoT data is unstructured, complex, frequently anonymized, streams in real-time, and often must be combined from numerous IoT devices – all of which have implications on the existing infrastructure.
On one hand, IoT generated data is sensitive, which impacts regulatory and compliance protocols. Additionally, IoT data is unstructured, complex, frequently anonymized, streams in real-time, and often must be combined from numerous IoT devices – all of which have implications on the existing infrastructure.
On the other hand, IoT data can provide a powerful competitive edge. CDPs with built-in IoT, artificial intelligence (AI) and machine learning (ML) capabilities offer critical advantages via automation, intelligence, segmentation, and prediction that helps maximize the potential of customer data. AI is able to discover patterns in data and analyze information to provide meaningful insights, in addition to performing complex customer segmentation. ML can identify customer segments and continuously self-learn to become smarter over time depending on the training data and models.
IoT-enabled, advanced CDP solutions offer benefits that can fuel a memorable Customer Experience.
● Sustainable personalization: Data security and privacy concerns are growing and we’re witnessing the end of third-party cookies. Advanced CDPs with real-time capabilities can help brands provide personalized experiences on the customer’s terms during critical moments.
● Augment inter-departmental data: The value of customer data isn’t limited to sales and marketing teams; it’s an enterprise-wide factor in organizational flexibility and transparency. CDPs offer streamlined integration with both external and legacy solutions to further augment existing data from other departments.
● Respond to emerging trends: As pressure to extend cohesive omnichannel experiences grows, organizations need the capabilities to instantly respond to fluctuating market trends or conditions. Advanced CDPs can enhance marketing efficiency and cost-effectiveness, and enable more robust agility to respond to constant change.
● Tailored marketing content: Brands can eradicate siloed marketing efforts per channel to provide more relevant, innovative marketing and sales content based on unique customer interests, such as product usage tips or interviews with a content creator.
Trends and Developments Shaping the IoT-Driven Customer Experience
Market momentum for CDPs is quickly evolving alongside technological advancement and adoption. In 2018, semiconductor firm ARM Limited acquired enterprise data platform provider, Treasure Data, to advance device-to-data IoT platform development.
Customer communications platform provider Twilio acquired CDP provider Segment for $3.2 billion in 2020 to improve their suite of customer engagement software and enable companies to extend connected CXs that revolve around high-quality data.
These examples demonstrate the market direction of CDP as a catalyst for an enriched CX. According to Gartner, by 2023 70% of independent CDP providers will be acquired by larger marketing technology vendors or will diversify through M&A to enter adjacent categories like multichannel marketing and personalization.
There are so many uses for IoT, in particular when AI and predictive analytics are integrated. Its not just global conglomerates in healthcare and medical devices. Many startups are building IoMT, aka the Internet of Medical Things, that allow doctors to monitor patients’ well-being remotely such as newest advances in heart monitoring and diabetes management. And of course there is the IoB aka the Internet of Behaviour that takes into account individual customer trends, location-based services marketing, and uses predictive analytic to discover accurate buying habit. Still others include IoLT aka the Internet of Logistics Things as in SCM, IoRT aka the Internet of Retail Things, and where DX all started and is evolving with IoWM aka the Internet of Workforce Management.
Future-Facing Customer Experience Programs will be Predictive
 Organizations today are collecting and integrating IoT data to produce rich customer insights. CX leaders who are looking to future-proof their CX programs are enhancing their data and analytics capabilities and looking to predictive insights to:
Organizations today are collecting and integrating IoT data to produce rich customer insights. CX leaders who are looking to future-proof their CX programs are enhancing their data and analytics capabilities and looking to predictive insights to:
● Build more connected customer experiences.
● Pinpoint CX obstacles and opportunities in real-time.
● Understand brand-to-consumer interactions on a deeper level.
● Prioritize customers at risk of churn and offer personalized solutions or compensation to stabilize the relationship.
● Gain a more holistic perspective of customer value potential.
With predictive insights from IoT data, brands can deliver rapid reimbursement for a shipping delay, or extend proactive customer service outreach when a customer is dealing with some issues in resolving a pain point, for example.
Predictive CDP systems provide companies with an opportunity to connect their Customer Experience programs to business value, such as enabling businesses to refine existing solutions that have a direct correlation to customer loyalty and up-sell behaviors.
According to Allen Proithis, CEO of Captone Partners, “Connected solutions are now table stakes for creating leading customer experiences. IoT data is the fuel for Digital Transformation, and the resulting Customer Experience is the destination. The faster that you can use data to fuel your transformation, the more quickly you will arrive at your ultimate customer experience that transforms the business relationship.”
The New Customer Experience Imperative
Marketers simply can’t afford to overlook the massive potential of IoT and other new technologies in their strategic CX initiatives. In a hyperconnected era defined by frictionless, data-driven, digital-first experiences across all channels and touchpoints, it’s either deliver a meaningful customer experience (CX) or become obsolete. To compete based on CX, organizations need to deploy the transformational power of IoT when it comes to their CDP.
If you need expertise utilizing a performance-based retained executive search within IoT, DX, or Customer Experience, check out what NextGen can offer you.


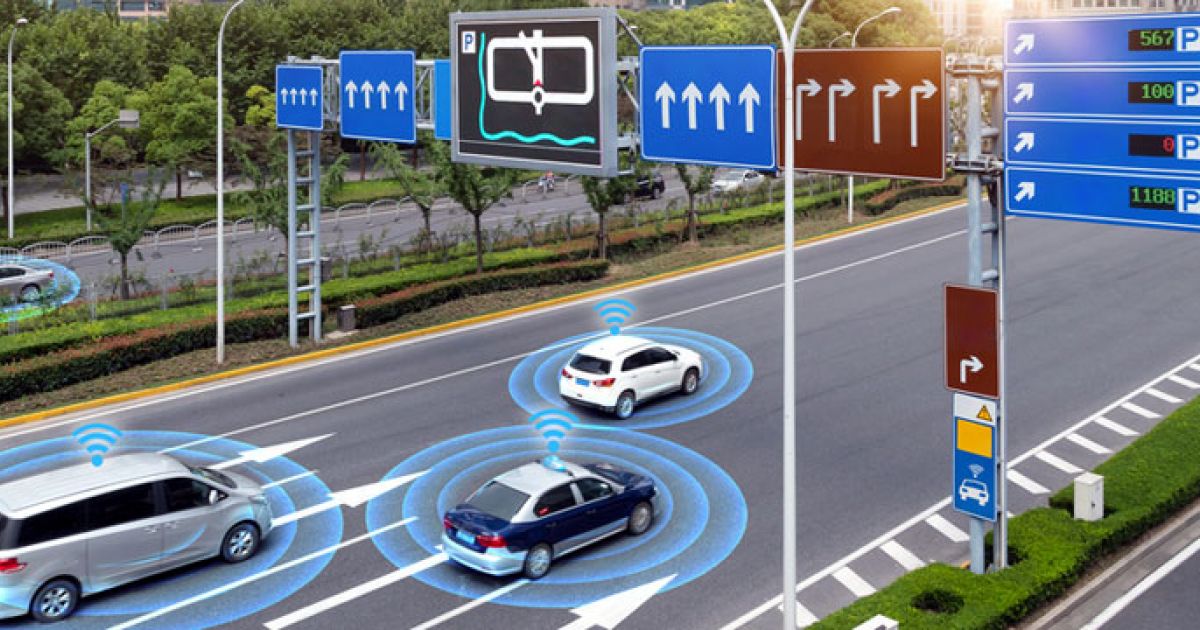
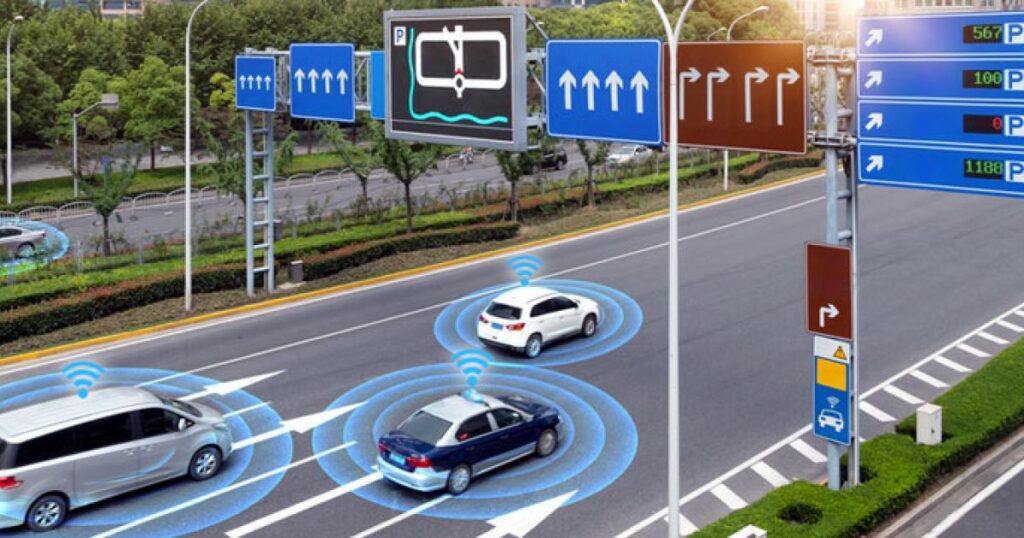 Will autonomous cars and other forms of transportation work without an IOT strategy? The challenge is not the lack of vision for IOT, the major issue is the lack centralized engineering standards and protocols. For an autonomous car to communicate with remote IOT sensors like stop lights, each sensor within the car will need to continued need to be operational and with the most updated software firm to insure predictable operations. The revolution of “Over the Air” software updates in real time became mainstream with the cell phone manufacturers like Samsung
Will autonomous cars and other forms of transportation work without an IOT strategy? The challenge is not the lack of vision for IOT, the major issue is the lack centralized engineering standards and protocols. For an autonomous car to communicate with remote IOT sensors like stop lights, each sensor within the car will need to continued need to be operational and with the most updated software firm to insure predictable operations. The revolution of “Over the Air” software updates in real time became mainstream with the cell phone manufacturers like Samsung 

 On one hand, IoT generated data is sensitive, which impacts regulatory and compliance protocols. Additionally, IoT data is unstructured, complex, frequently anonymized, streams in real-time, and often must be combined from numerous IoT devices – all of which have implications on the existing infrastructure.
On one hand, IoT generated data is sensitive, which impacts regulatory and compliance protocols. Additionally, IoT data is unstructured, complex, frequently anonymized, streams in real-time, and often must be combined from numerous IoT devices – all of which have implications on the existing infrastructure. Organizations today are collecting and integrating IoT data to produce rich customer insights. CX leaders who are looking to future-proof their CX programs are enhancing their data and analytics capabilities and looking to predictive insights to:
Organizations today are collecting and integrating IoT data to produce rich customer insights. CX leaders who are looking to future-proof their CX programs are enhancing their data and analytics capabilities and looking to predictive insights to: The Covid-19 pandemic has also pushed the demand for high speed Internet into overdrive. High-speed connectivity has emerged as a necessity and the promise of fifth-generation is delivering for business use cases that rely on the growing network of IoT technologies and data streaming. Progressive organizations that have embraced the combination of 5G connectivity and IoT technologies generating massive data sets in real-time, at higher velocity and across a growing network of nodes. The result are digital initiatives that promise intelligent, data-driven transformation, new operational workflows and unprecedented new business model innovations.
The Covid-19 pandemic has also pushed the demand for high speed Internet into overdrive. High-speed connectivity has emerged as a necessity and the promise of fifth-generation is delivering for business use cases that rely on the growing network of IoT technologies and data streaming. Progressive organizations that have embraced the combination of 5G connectivity and IoT technologies generating massive data sets in real-time, at higher velocity and across a growing network of nodes. The result are digital initiatives that promise intelligent, data-driven transformation, new operational workflows and unprecedented new business model innovations.

 Proper training for every step only makes sense. All medical professionals are bound under an ethics code with severe penalties for infringement. There have not yet been any serious attacks on medical IoT’s.
Proper training for every step only makes sense. All medical professionals are bound under an ethics code with severe penalties for infringement. There have not yet been any serious attacks on medical IoT’s.
 German designer Clemens Weisshaar addressed the issue in a form at Vienna Design Week in 2014. “Taking robots online is as dangerous as anything you can put on the web,” he said.
German designer Clemens Weisshaar addressed the issue in a form at Vienna Design Week in 2014. “Taking robots online is as dangerous as anything you can put on the web,” he said. 
 From a technology viewpoint, implant solutions have to resolve trade-offs associated with efficiency and accuracy against antenna size, power use, operating bandwidth and materials costs. Moreover, implant devices should be appropriate for various body and skin morphologies, while at the same time offering security and data protection features that render them immune to malicious parties that may attempt to compromise their operation.
From a technology viewpoint, implant solutions have to resolve trade-offs associated with efficiency and accuracy against antenna size, power use, operating bandwidth and materials costs. Moreover, implant devices should be appropriate for various body and skin morphologies, while at the same time offering security and data protection features that render them immune to malicious parties that may attempt to compromise their operation.